In today's Edworking News, we delve into a fascinating and somewhat alarming story about how a billion-dollar venture capital firm was compromised using a simple inspect element trick. The story begins with a cybersecurity enthusiast who enjoys searching Twitter for companies to perform quick penetration tests. This method has proven to be surprisingly effective.
During one of these searches, the enthusiast used the "Relevant People" tab on Twitter, which led them to the venture capital firm a16z. The hacker then performed a subdomain scan and used tools from Lunchcat to check for common vulnerabilities, such as secrets in JavaScript files. This routine scan led to the discovery of portfolio.a16z.com, a portfolio management tool for companies associated with a16z.
While performing cursory checks, Lunchcat flagged an AWS key referenced somewhere on the website. Upon further inspection, the hacker found the entire process.env of a Heroku instance embedded in the JavaScript, dynamically inserted. This was a significant find, as it meant that anyone could access these credentials simply by using the inspect element feature in their browser.
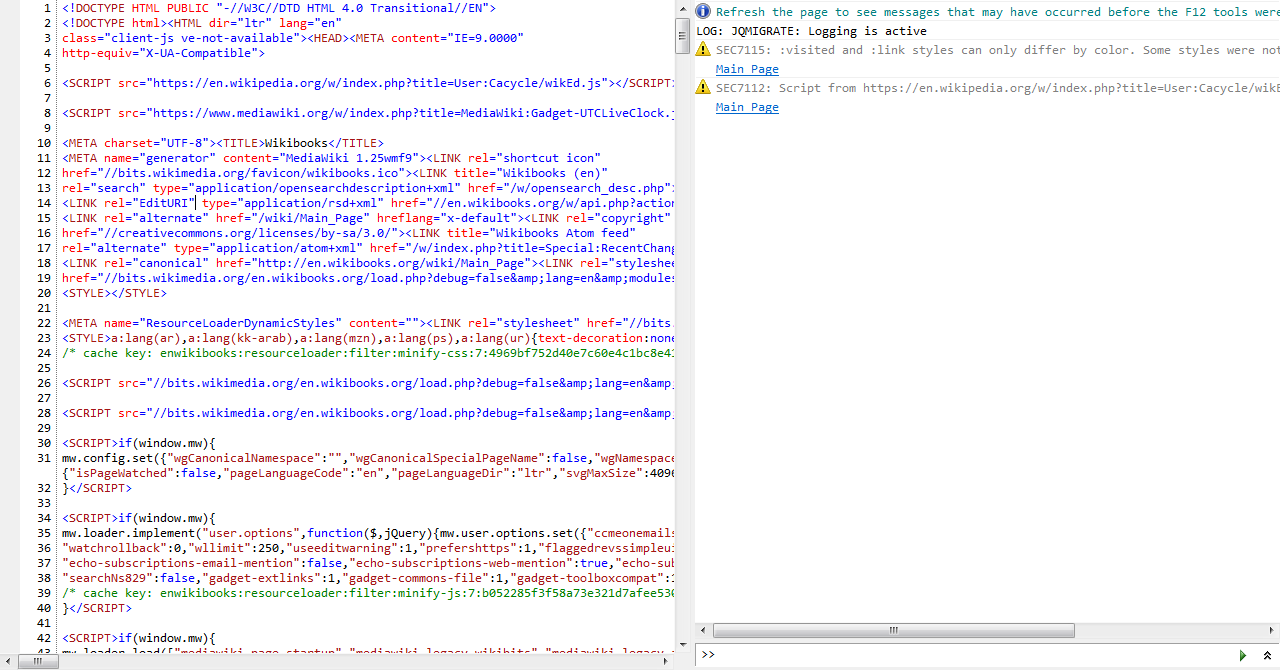
Image: Inspect Element revealing sensitive information
The credentials were verified and found to be real, posing a severe security risk. The compromised services included various critical components, but the hacker did not receive any bug bounty from a16z. The reason given was that the hacker had publicly reached out instead of contacting the firm privately. This decision was made because the hacker felt it was unfair to be ignored or dismissed.
For more details, you can read the related TechCrunch article, where journalist Lorenzo reached out to the hacker after seeing their tweet and wrote a comprehensive piece on the incident.

 Remember these 3 key ideas for your startup:
Remember these 3 key ideas for your startup:
- Regular Security Audits: Ensure that your web applications undergo regular security audits. Tools like Lunchcat can help identify vulnerabilities such as exposed AWS keys or other sensitive information in your JavaScript files. Regular audits can prevent such critical data from being exposed.
- Private Disclosure Channels: Establish clear channels for security researchers to report vulnerabilities privately. This not only helps in addressing the issue discreetly but also encourages ethical hacking practices. Offering bug bounties can incentivize researchers to report issues responsibly. For more on setting up effective communication channels, see how to create an effective document management workflow.
- Environment Variables Management: Be cautious about how and where you store your environment variables. Avoid embedding them directly in your JavaScript files. Use secure methods to manage and access these variables to prevent unauthorized access. Learn more about task automation and why you should use it to streamline your processes.
Edworking is the best and smartest decision for SMEs and startups to be more productive. Edworking is a FREE superapp of productivity that includes all you need for work powered by AI in the same superapp, connecting Task Management, Docs, Chat, Videocall, and File Management. Save money today by not paying for Slack, Trello, Dropbox, Zoom, and Notion. For more details, see the original source.