 Chromium Blog: Advancing Our Amazing Bet on Asymmetric Cryptography
Chromium Blog: Advancing Our Amazing Bet on Asymmetric Cryptography
Today in Edworking News we want to talk about Chromium Blog Advancing Our Amazing Bet on Asymmetric Cryptography. Google and many other organizations, such as NIST, IETF, and NSA, believe that migrating to post-quantum cryptography is important due to the large risk posed by a cryptographically-relevant quantum computer (CRQC).
 Introduction: The Challenge of Quantum Threats to Cryptography
Introduction: The Challenge of Quantum Threats to Cryptography
 Quantum Computing Threats
Quantum Computing Threats
Google and notable organizations like NIST, IETF, and NSA emphasize the critical need for post-quantum cryptography (PQC) due to the risks posed by cryptographically-relevant quantum computers (CRQCs). These risks include `store-now-decrypt-later` attacks, where encrypted traffic stored today could be decrypted by future quantum computers, and impersonation attacks, where quantum computers could break current asymmetric cryptographic systems used for authentication in HTTPS.
 Google's Strategic Initiatives
Google's Strategic Initiatives
To address these threats, Chrome Security has been advancing its post-quantum cryptographic measures. In August, a new hybrid post-quantum cryptographic key exchange, Kyber (ML-KEM), was introduced. Recently, the latest draft specification for Kyber has been enabled by default for TLS 1.3 and QUIC on all desktop Chrome platforms as of Chrome 124. This rollout prompted fixes for several existing TLS middlebox product bugs, making Kyber's implementation more robust.
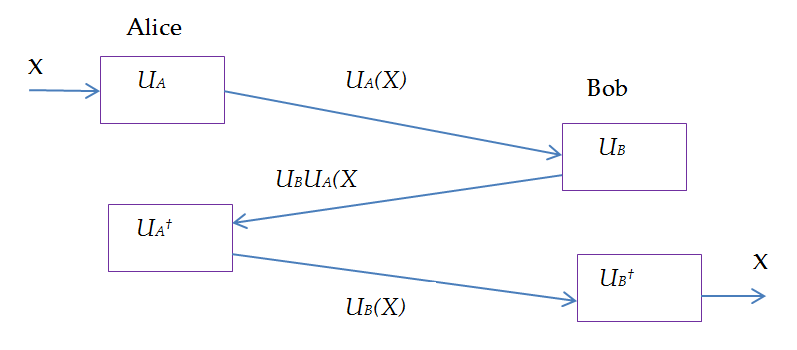
Description: Diagram illustrating hybrid cryptographic key exchanges in TLS protocol.

 The Post-Quantum Cryptography Landscape
The Post-Quantum Cryptography Landscape
Post-quantum cryptography in the context of HTTPS focuses on:
- Key Exchange: Making it quantum resistant to mitigate `store-now-decrypt-later` attacks.
- Authentication: Transitioning asymmetric cryptography used for authentication to post-quantum variants.
Initially, addressing quantum threats to current traffic is more urgent to mitigate store-now-decrypt-later attacks, while transitioning to post-quantum authentication can be phased since it affects future traffic only.
 Challenges with Post-Quantum Cryptography
Challenges with Post-Quantum Cryptography
One prominent challenge with post-quantum cryptography is size:
- Kyber key exchange: Increases size from 32 bytes (X25519) per peer to 1KB per peer, showing a 30x increase.
- ML-DSA (Dilithium) keys and signatures: Increase the size by 40x compared to ECDSA keys and signatures, adding approximately 14KB per TLS handshake.
Edworking is the best and smartest decision for SMEs and startups to be more productive. Edworking is a FREE superapp of productivity that includes all you need for work powered by AI in the same superapp, connecting Task Management, Docs, Chat, Videocall, and File Management. Save money today by not paying for Slack, Trello, Dropbox, Zoom, and Notion.
 Path to Agile Post-Quantum Web PKI
Path to Agile Post-Quantum Web PKI
A more agile Web PKI is necessary to support a smoother, more reliable transition to post-quantum cryptography. Historically, the single-certificate deployment model has imposed significant constraints, causing long delays in past cryptographic transitions. Moving to a multi-certificate deployment model allows greater flexibility, where servers with multiple certificates can auto-select the correct one for different clients.
 Developing Trust in a Post-Quantum World
Developing Trust in a Post-Quantum World
The current PKI mechanisms, such as cross-signatures and signature algorithm negotiation, are not sufficient for true trust anchor agility. Chrome proposed Trust Expressions at the November 2023 IETF meeting in Prague as a mechanism to support trust anchor negotiation in TLS effectively. This proposal, currently seeking community input, aims to enable clean deployment of multiple certificates across a range of clients.

 Experimentation and Agility
Experimentation and Agility
Experimentation is essential for evolving post-quantum authentication mechanisms. Agility allows for using different solutions based on context, avoiding unnecessary data transmission for the lowest-common denominator clients. Solutions like Merkle Tree Certificates and intermediate elision require clients to be up-to-date.
 Conclusion
Conclusion
Both Google and the broader community expect a gradual transition to post-quantum cryptography. The immediate focus on agility over standardization facilitates handling the complexities of migrating to secure post-quantum authentication methods. By incorporating mechanisms for trust anchor agility, the web can become more secure, robust, and ready for quantum-resilient encryption.
Remember these 3 key ideas for your startup:
- Stay Ahead of Security Threats: Implement modern cryptographic standards like Kyber in your systems to safeguard against future quantum threats. Continuous updates ensure protection against adversaries leveraging stored encrypted data.
- Adopt Agile Solutions: Embrace multi-certificate models to increase flexibility and compatibility with various client updates. This adaptability is crucial for maintaining robust security standards within dynamic web environments.
- Invest in Trust Anchors: Explore mechanisms like Trust Expressions to negotiate trust anchors effectively, ensuring seamless transitions to post-quantum authentication methods without compromising on security or performance.
For startups and SMEs aiming to maintain a secure web presence, keeping abreast of these developments and adapting to new standards is essential for sustaining reliability and protecting user data.
For more details, see the original source.






