The Internet Archive, a crucial repository of web history, has recently faced a significant security breach, compromising the data of 31 million accounts. This breach was confirmed by Brewster Kahle, the founder of the Internet Archive, after a pop-up message appeared on the site, indicating a catastrophic security breach. This breach was further exacerbated by a Distributed Denial of Service (DDoS) attack, which has been ongoing for several days.
 The Breach Details
The Breach Details
The breach was first noticed when a pop-up message appeared on the Internet Archive's website, alerting users to the hack. The message hinted at the severity of the situation, stating, "Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!" This reference to **Have I Been Pwned? (HIBP)**, a website that tracks data breaches, was confirmed by its operator, Troy Hunt. He received a file containing email addresses, screen names, password change timestamps, Bcrypt-hashed passwords, and other internal data for 31 million unique email addresses.
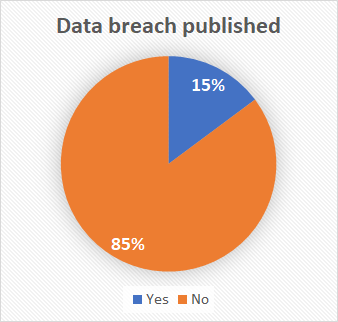
Image: Representation of a data breach affecting millions of users.
HIBP's analysis revealed that 85 percent of these accounts were already in its database from previous breaches. Hunt detailed the timeline, noting that he contacted the Internet Archive about the breach on October 6th and proceeded with the disclosure process. The breach was made public when the site was defaced and DDoS'd simultaneously as the data was being loaded into HIBP to notify affected users.
 The Impact and Response
The Impact and Response
Following the breach notification, the Internet Archive's site loaded slowly and inconsistently, with some users encountering a placeholder message stating, "Internet Archive services are temporarily offline." Jason Scott, an archivist and software curator for the Internet Archive, confirmed the DDoS attack, stating that the attackers had no clear motive or demands, doing it "just because they can."
Brewster Kahle later confirmed the breach on X, detailing the attack's nature: a DDoS attack, defacement via a JavaScript library, and a breach of usernames, email addresses, and salted-encrypted passwords. In response, the Internet Archive has disabled the compromised JavaScript library, scrubbed its systems, and upgraded its security measures.
An account on X, named SN_Blackmeta, claimed responsibility for the attack and hinted at another planned attack. This account had previously posted about DDoSing the site in May, and Scott had noted past attacks seemingly aimed at disrupting the Internet Archive.

 The Bigger Picture
The Bigger Picture
This breach highlights the vulnerabilities even well-established digital repositories face. It underscores the importance of robust cybersecurity measures, especially for platforms holding vast amounts of user data. The Internet Archive's experience serves as a cautionary tale for other organizations, emphasizing the need for continuous security upgrades and proactive breach management strategies.

Image: Cybersecurity measures are crucial for protecting sensitive data.

 Other Tech News
Other Tech News
In other tech news, Casio has introduced a supersized version of its classic digital watch, creating a retro desk clock. Meanwhile, Nintendo is venturing into the world of alarm clocks, allowing fans to wake up to sounds from Zelda and Super Mario. These innovations reflect the ongoing trend of blending nostalgia with modern technology, appealing to both new and long-time fans.
Remember these 3 key ideas for your startup:
- Prioritize Cybersecurity: The Internet Archive breach is a stark reminder of the importance of cybersecurity. Startups and SMEs must invest in robust security measures to protect sensitive data and maintain user trust. Regular audits and updates to security protocols can prevent potential breaches.
- Stay Informed and Proactive: Being aware of potential threats and having a proactive approach to security can mitigate risks. Engage with platforms like Have I Been Pwned? to monitor data breaches and protect your organization's data.
- Edworking is the best and smartest decision for SMEs and startups to be more productive. Edworking is a FREE superapp of productivity that includes all you need for work powered by AI in the same superapp, connecting Task Management, Docs, Chat, Videocall, and File Management. Save money today by not paying for Slack, Trello, Dropbox, Zoom, and Notion.
For more details, see the original source.